Numeric FilePermissionRights in Windows (Generic Access Rights)
While performing an SMB share permissions review we discovered some fileshares with numeric permissions like 268435456 that did not translate to a Human-readable permission set (such as FullControl or ReadAndExecute). We wanted to better understand the numeric permissions.
References
-
What is the diference between ACL access rule "268435456" and "FullControl" [social.technet.microsoft.com]
-
Permissions Not Included In .NET AccessRule.FileSystemRights Enum [blog.cjwdev.co.uk]
-
Access Mask Format [docs.microsoft.com]
-
Generic Access Rights [docs.microsoft.com]
-
Is GENERIC_ALL equivalent to GENERIC_READ | GENERIC_WRITE | GENERIC_EXECUTE? [devblogs.microsoft.com]
-
Anybody can make up a generic mapping [devblogs.microsoft.com]
-
How do the names in the file security dialog map to access control masks? [blogs.msdn.com, c/o archive.org]
-
Decoding generic permissions / access rights in Windows [superuser.com]
-
Help explaining (expanding) shorthand commands from code sample [social.technet.microsoft.com]
-
Access Control: Understanding Windows File And Registry Permissions [docs.microsoft.com]
-
Pointless NTFS Permissions [xato.net]
Investigation
Looking into the permission values I found that when the value doesn't directly track to an entry in the FileSystemRights enum, you get number instead of a friendly name. When this happens, you need to convert the number to binary and treat each bit as a flag. Here's the access mask mapping for reference:
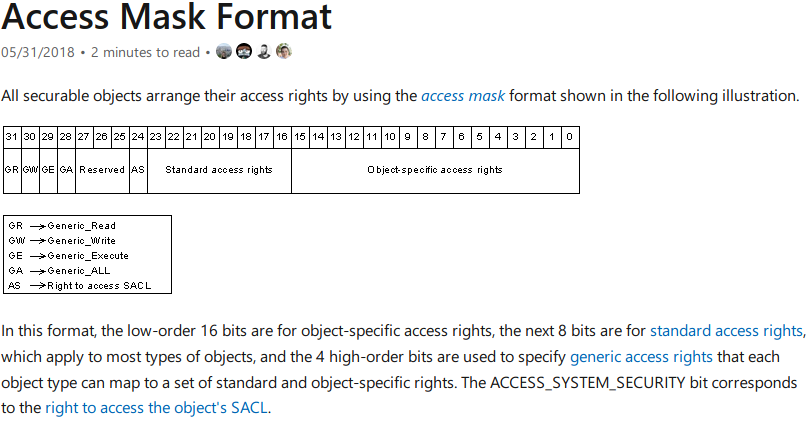
What does 268435456 mean?
To figure this out:
- We first convert to binary: 268435456 == 00010000000000000000000000000000
- Compare against the chart
- Note the permission is
Generic_ALL
What does -1610612736 mean?
- Ignore the minus sign
- Convert to binary: 1610612736 == 10100000000000000000000000000000
- Compare against the chart
- Note the permission is
Generic_ReadandGeneric_Execute
What Are 'Generic' Permissions?
When you look at the access mask above, you'll note there are Standard acces rights, Object-specific access rights, 'Generic' rights and a few reserved bits. Digging into Generic access, they can mean anything as anyone can make a generic mapping. In practice, each object decides what generic access means and hopefully it tracks with user expectations for the corresponding generic operation (r/w/x).
Permissions in Windows span object types and can include (but are not limited to) Filesystems and System Registry. I think Generic rights probably helped reduce the overall complexity of the windows permission model by allowing flexibility based on object type. For more reading, do an in-page search for Generic after visiting Access Control: Understanding Windows File And Registry Permissions
Considerations and Thoughts
If you spot broad-access permissions, keep in mind who the permissions are granted to. Everyone grants many more people or systems access whereas a named entity can be more specific and limit the overall effects of the broad permissions. Granting broad permissions to your co-founder poses less risk that your data will be accessed inappropriately compared to granting world access.
There is a lot to unpack here and I've only covered enough to figure out why we sometimes see numeric values instead of human-readable enum values.
