Configure Centos 7 and OpenLDAP for secure connections
As part of a network infrastructure refresh I ended up rebuilding our OpenLDAP and Samba servers so they would play nicely with each other. Configuring OpenLDAP is a non-trivial exercise which required examining dozens of web pages and PDFs to get the information I needed to complete my task.
Unfortunately, most resources out there on the internet revolve around configuring the slapd.conf file, which isn't a viable solution when standing up a new server given that OpenLDAP uses a newer and much more confusing system to store its settings.
This guide will walk through setting up OpenLDAP server that communicates using a self-signed certificate (LDAPS over port 636) and that has the appropriate schema files which allow a separate samba server to leverage OpenLDAP for share permissions (configuring Samba is a different article for another day!)
As part of a network infrastructure refresh I ended up rebuilding our OpenLDAP and Samba servers so they would play nicely with each other. Configuring OpenLDAP is a non-trivial exercise which required examining dozens of web pages and PDFs to get the information I needed to complete my task.
Unfortunately, most resources out there on the internet revolve around configuring the slapd.conf file, which isn't a viable solution when standing up a new server given that OpenLDAP uses a newer and much more confusing system to store its settings.
This guide will walk through setting up OpenLDAP server that communicates using a self-signed certificate (LDAPS over port 636) and that has the appropriate schema files which allow a separate samba server to leverage OpenLDAP for share permissions (configuring Samba is a different article for another day!)
References
- LDAP-based authentication for Samba [ibm.com]
- OpenLdap 2.4 on centos 6 doesn't listen on port 636 [serverfault.com]
- Step by Step OpenLDAP Server Configuration on RHEL7/Centos7 [learnitguide.net]
- RHEL7: Configure a LDAP directory service for user connection. [certdepot.net]
- LDAP for Rocket Scientists [zytrax.com]
Install OpenLDAP Packages
yum install openldap-servers openldap-clients migrationtools
Create Self-Signed certificate
openssl req -new -x509 -nodes -out /etc/openldap/certs/dit.domain.tld.pem -keyout /etc/openldap/certs/dit.domain.tld.key.pem -days 720Note 1: We'll come back to this later. This is a pre-requisite to run a secure ldap installation
Note 2: replace any instance of dit.domain.tld with the FQDN of your LDAP Server!
Note 3: If you need other people to interact with your LDAP Server, consider purchasing a certificate signed by a Certificate Authority. While a self-signed cert can work fine in a lot of instances, your administration overhead scales linearly with the number of computers that need to hit your server.
Ensure Certificate and Key permissions are adequate
chown ldap:ldap /etc/openldap/certs/dit.domain.tld.pem
chown ldap:ldap /etc/openldap/certs/dit.domain.tld.key.pem
chmod 640 /etc/openldap/certs/dit.domain.tld.key.pemCreate an OpenLDAP root / admin user password
We'll get around to creating the root user in the OpenLDAP Directory later. For now, we need the hashed password for configuration purposes.
slappasswd
(This command will return a hash: remember both the hash and the password you used to generate it!)
Configure the OpenLDAP cn=config / olc database with basics
In older versions of OpenLDAP we would only have to modify the slapd.conf file. Unfortunately (or fortunately, depending on how you look at it?) we need to deal with more complicated configurations. Practically speaking this means we need to edit an ldif file with an obscure name and make some settings changes.
What is an ldif file, you might be asking? It stands for LDAP Data Interchange Format and lets us create LDAP configs that in theory can be portable to some degree (wikipedia for more info).
Other questions you might have could be 'what is cn=config?' and 'why is there so little practical documentation around this new way of doing things?'. Both would be valid questions. This link from the LDAP for Rocket Scientists online book might help you with your first question. Unfortunately, I can't answer question 2.
So, let's get on with our adventure! Here are the steps to edit your olcDatabase={2}hdb.ldif file with the necessary details:
Important Note: The configuration file will have a message at the top which indicates that you should use something called ldapmodify to make changes to this file. I couldn't get this to work and I don't know how it works anyway, so I'm taking you down the manual-edit path. This will generate some warnings later on, so if you feel strongly about that I suggest looking up how to use ldapmodify since I won't be covering it
- nano /etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif
- Edit the olcSuffic and olcRootDN so they look like this (** Remember to replace your domain info!):
olcSuffix: dc=domain,dc=tld
olcRootDN: cn=admin,dc=domain,dc=tld -
Add these lines to the end of the file:
olcRootPW: <HASH FROM THE CREATE ROOT / ADMIN PASSWORD STEP ABOVE>
olcTLSCipherSuite: HIGH
olcTLSCertificateFile: /etc/openldap/certs/dit.domain.tld.pem
olcTLSCertificateKeyFile: /etc/openldap/certs/dit.domain.tld.key.pem
When you are finished making your edits, you should have a file that looks something like this:
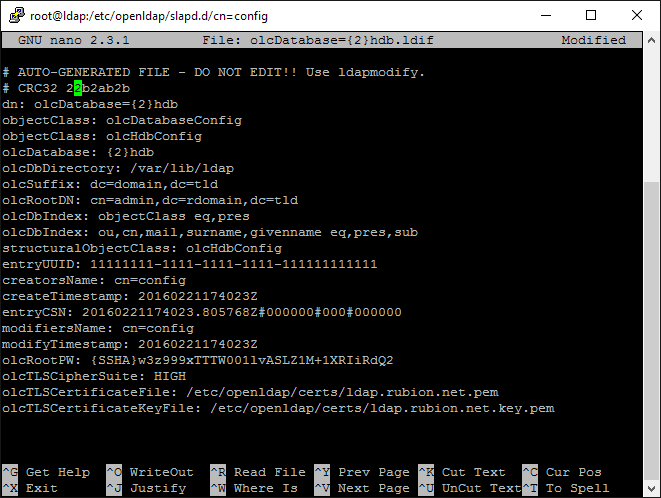
(I hope this is helpful: as I was assembling this post I wished someone would have given me a dump of what to expect from the file!)
Enable Secure LDAP (LDAPS)
Now that we have our basic configuration in place we can turn on LDAPS. To do this we need to open the slapd configuration file and make one edit and add one line. When finished, the self-signed certificate we created above will be used to secure LDAP traffic:
- nano /etc/sysconfig/slapd
- Edit the SLAPD_URLS line to look like this (add an 's' to the ldap:/// entry):
SLAPD_URLS="ldapi:/// ldaps:///"
- Add this line to to the file:
SLAPD_LDAPS=yes
When finished, the file will look something like this:
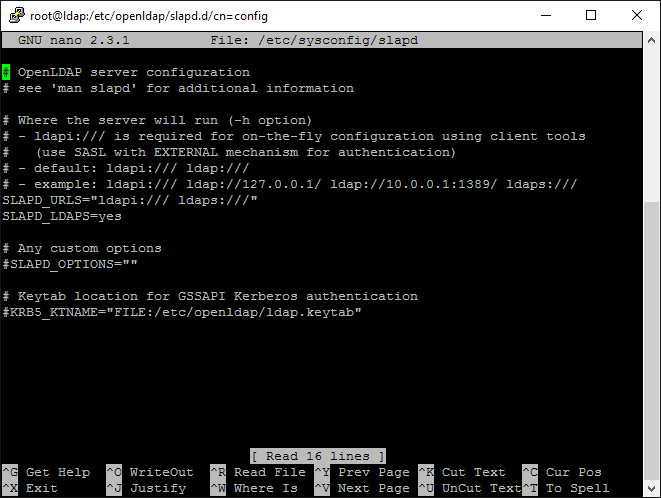
One More cn=config / olc Change for 'Monitor' Privileges
I don't really know what 'monitor' privileges are or why I would need them. However, the path I took to a working LDAP server passed through setting this up, so I include it here:
- nano /etc/openldap/slapd.d/cn=config/olcDatabase={1}monitor.ldif
- edit the olcAccess entry to reflect your admin/root/manager login (whatever you chose it to be in the last cn=config file we edited above):
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=extern
al,cn=auth" read by dn.base="cn=admin,dc=domain,dc=tld" read by * none
When finished the file will look something like this:
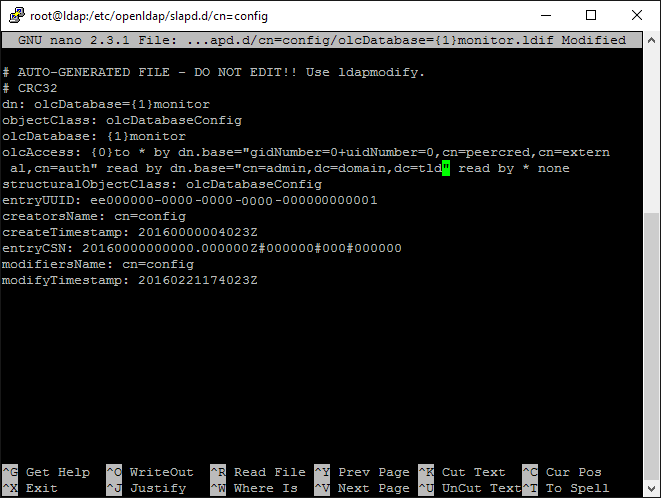
Validity Check of OpenLDAP configuration
Ok, with all the magic we've wrought we should be good to go. Just to be sure, let's run the validation utility:
slaptest -u
(I mentioned earlier that we'll see warnings by hand-editing these files. You'll see the warnings here)
If all goes well, you'll see a message that says config file testing succeeded. This should mean we're good to go!
Here's what that should look like:
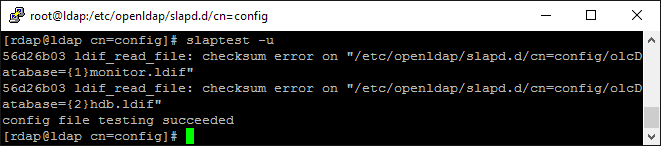
Start the LDAP Service
Ok, we're about halfway through! Now we need to enable / start the ldap service so we can actually add things to our OpenLDAP Database:
- systemctl enable slapd
- systemctl start slapd
Configure the LDAP Database (Including Basic Schemas)
Now that the service is running we need to configure our database. There is a sample database config that is included with Centos 7 that we can use. I left it as-is since my needs are pretty basic. To use it we need to copy the config file to a new place and change ownership:
- cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
- chown ldap:ldap /var/lib/ldap/DB_CONFIG
Ok, that looks good. Now we need to add 'schemas' to the database. Without schemas, nothing works since nothing is defined. You can't have an inetorgperson without it being defined first! There are several schemas included with Centos 7 which can be found in the /etc/openldap/schema directory. We'll grab 3 here, then get crazy and add a 4th in the next section:
- ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
- ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
- ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
(Yeah, these sound pretty crazy- I'd like to find out some day why these are named the way they are...)
Add the Samba LDAP Schema
Ok, we have a depenency here. In order to add the Samba LDAP schema we need to have a samba server already installed (not necessarily configured). You'll need to pull a file from the samba server over to the LDAP Server to make this work:
- File to copy from the samba server: /usr/share/doc/samba-4.2.3/LDAP/samba.ldif
- Location on LDAP Server to copy the file to: /etc/openldap/schemas/samba.ldif
- Load the schema like this:
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/samba.ldif
At this point we have all the LDAP Schemas we need to make things work (yay!)
Create an Ugly Organizational LDIF File
Now we're into customization land (as if we haven't been there for the last hour). This is the place where you can define how **YOUR** OpenLDAP structure will be defined. We need to include the root/base/admin user, a place for users, and anything else you need. My example configuration here is rudimentary and experimental, but it seemed to work on my prototype server:
Important Note: Be sure that every blank line in your file is empty except for newline characters, otherwise you'll complicate things for yourself!
Important Note 2: Be sure include a space between any line and a line starting with dn:. I don't claim to understand why the parser works the way it does, but be forewarned: things won't work if there is no blank line before each dn: entry.
Important Note 3: each dn: entry **MUST** have a SINGLE space after the colon and before the entry information. Again, this is a formatting requirement- I didn't engineer it.
####
#### You can use the ldapadd command to bootstrap this damn thing.
#### Based off of: http://www.zytrax.com/books/ldap/ch5/
####
#### The blank lines before each 'dn:' entry are required for some indeterminate reason
#### Also: the space immediately after 'dn:' is vitally required as well...
####
##
## Configure the 'base/root'
dn: dc=domain,dc=tld
dc: domain
description: user directory for the domain.tld domain
objectClass: dcObject
objectClass: organization
o: domain network
##
## Configure the Directory Manager
dn: cn=admin,dc=domain,dc=tld
objectClass: organizationalRole
cn: admin
description: I am the directory manager
##
## Configure the USERS hierarchy (non-admins)
dn: ou=users, dc=domain,dc=tld
ou: users
description: all non-admin (non-root) users
objectclass: organizationalunit
##
## Configure the ADMINS hierearchy
dn: ou=admins, dc=domain,dc=tld
ou: admins
description: Admin users hierarchy
objectclass: organizationalunit
Once the file is saved, you can 'activate' it by running the ldapadd command. We need to specify the FULL DN to our administrator/root/base user in this command line:
ldapadd -x -W -D "cn=root,dc=domain,dc=tld" -f ~/configzzz/dit.domain.tld.ldif
Now we want to make sure that it worked by running a quick ldapsearch:
ldapsearch -x cn=admin -b dc=domain,dc=tld
If you see information coming back, you're good!
Firewall rule configuration
Now we need to make sure the firewall will let through legitimate ldap requests over the secure port:
- firewall-cmd --permanent --add-service=ldaps
- firewall-cmd --reload
Troubleshooting
Q: Hey wise-guy, I can't get ldapadd or ldapsearch or anything to work. I just get this message:
ldap_sasl_bind(SIMPLE): Can't contact LDAP server
A: Wow, that's ugly! I'd go back to the step where we disable regular ldap in favor of ldaps and change it back to insecure mode (in /etc/sysconfig/slapd), perform the steps, then disable it. Looks like there can be issues getting the command line tools to connect to a local secure instance that does not advertise insecure authentication as well.
Next Steps
Fire up an LDAP Browser and add your users, groups and machines. You could use the CLI, but why bother when a nice GUI tool is well suited for one-off additions and group administration. I like the LDAP Admin software for Windows based systems.
Next article should be about setting up Samba to use LDAP for share permissions, so stay tuned!
